00:文章简介
使用OpenLDAP+freeradius+802.1x实现了无线和有线网络认证+动态vlan下发,这是一个综合案例,里面涉及了加密和密码自助修改等。
理想示意图

01:环境准备
1.1:服务器环境信息
| 名称 | 系统版本 | 配置 | ip地址 |
|---|---|---|---|
| ldap-master | CentOS 7.6(core) | 2c 2g 50g | 192.168.2.147 |
| ldap-slave | CentOS 7.6(core) | 2c 2g 50g | 192.168.2.150 |
| redius-master | CentOS 7.6(core) | 2c 2g 50g | 192.168.3.140 |
| redius-slave | CentOS 7.6(core) | 2c 2g 50g | 192.168.3.141 |
| CA服务器 | CentOS 7.6(core) | 1c 1g 16g | 192.168.2.148 |
| 客户机 | Windows7 | 2c 2g 50g | 192.168.3.150 |
(地址非上线时地址,只做临时演示使用。)
1.2:初始化服务器配置
(脚本里的网卡名称要注意)
#/bin/bash
echo "Enter your system information"
###关闭防火墙、NetworkManager、SELinux###
systemctl stop firewalld
systemctl disable firewalld
systemctl stop NetworkManager
systemctl disable NetworkManager
setenforce 0
sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config
###关闭防火墙、NetworkManager、SELinux###
##安装一些常用的软件##
yum -y install vim tree wget net-tools ntpdate
###同步时间
ntpdate ntp1.aliyun.com
echo "* */1 * * * /usr/sbin/ntpdate ntp1.aliyun.com > /dev/null 2>&1" > /var/spool/cron/root
##更改yum源为阿里云源
mkdir /etc/yum.repos.d.bak ; mv /etc/yum.repos.d/* /etc/yum.repos.d.bak
wget -O /etc/yum.repos.d/aliyun-centos7-base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
wget -O /etc/yum.repos.d/aliyun-centos7-epel.repo http://mirrors.aliyun.com/repo/epel-7.repo
yum clean all
yum makecache
####网卡配置
m1=`ifconfig ens192 | grep "ether"| tr -s " " %|cut -d% -f3`
cd /etc/sysconfig/network-scripts/
echo "HWADDR=$m1" >> ifcfg-ens192
mv ifcfg-ens192 ifcfg-eth0
sed -i 's/ens192/eth0/g' ifcfg-eth0
cat > /etc/udev/rules.d/70-persistent-net.rules <<EOF
SUBSYSTEM=="net",ACTION=="add",DRIVERS=="?*",ATTR{address}=="$m1",ATTR{type}=="1",KERNEL=="eth*",NAME="eth0"
EOF
##创建几个需要的文件夹
mkdir /data
###PS1
echo 'export PS1="\[\e[37;40m\][\[\e[31;40m\]\u\[\e[37;40m\]@\h \[\e[36;40m\](\t)\w\[\e[0m\]]\\$ "' >> /root/.bashrc
1.3:保存快照防止误操作导致系统崩溃
重启后开始部署ldap环境
02:LDAP环境搭建
2.1:确保已联网
[root@lcp (13:49:35)~]# ping www.baidu.com
PING www.a.shifen.com (61.135.169.125) 56(84) bytes of data.
64 bytes from 61.135.169.125 (61.135.169.125): icmp_seq=1 ttl=128 time=3.11 ms
^C
--- www.a.shifen.com ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 3.111/3.111/3.111/0.000 ms
2.2:安装所需软件包
[root@ldap-master (11:21:26)~]# yum -y install openldap openldap-servers openldap-clients compat-openldap openldap-devel migrationtools samba* freeradius*
2.3:LDAP配置文件存放目录
[root@ldap-master (11:21:26)~]# cd /etc/openldap/
[root@ldap-master (11:25:33)/etc/openldap]# tree slapd.d
slapd.d
├── cn=config
│ ├── cn=schema
│ │ └── cn={0}core.ldif #核心配置文件
│ ├── cn=schema.ldif #schema配置文件
│ ├── olcDatabase={0}config.ldif #关于全局的配置文件
│ ├── olcDatabase={-1}frontend.ldif #关于前端的配置文件
│ ├── olcDatabase={1}monitor.ldif #关于监控的配置文件
│ └── olcDatabase={2}hdb.ldif #关于数据库的配置文件
└── cn=config.ldif #关于全局配置的文件
2 directories, 7 files
2.4:配置LDAP
2.4.1:备份配置文件目录
[root@ldap-master (11:25:35)/etc/openldap]# mv slapd.d{,.bak}
[root@ldap-master (11:26:16)/etc/openldap]# ls
certs check_password.conf ldap.conf schema slapd.d.bak
[root@ldap-master (11:26:23)/etc/openldap]# mkdir slapd.d
[root@ldap-master (11:26:30)/etc/openldap]# slappasswd
New password: 123456
Re-enter new password: 123456
{SSHA}hnxiKpbSXyzF1sazYma5FBlkdD39dpU6 #复制保存好,一会要用到
[root@ldap-master (11:26:43)/etc/openldap]# cp /usr/share/openldap-servers/slapd.ldif ./ #复制slapd.ldif配置文件到此目录下
2.4.2:复制需要的schema到/etc/openldap/schema目录下
这里把samba和radius的schema都复制过来。
cp /usr/share/doc/freeradius-3.0.13/schemas/ldap/openldap/freeradius.ldif /etc/openldap/schema/
cp /usr/share/doc/freeradius-3.0.13/schemas/ldap/openldap/freeradius.schema /etc/openldap/schema/
cp /usr/share/doc/samba-4.9.1/LDAP/samba.schema /etc/openldap/schema/
cp /usr/share/doc/samba-4.9.1/LDAP/samba.ldif /etc/openldap/schema/
2.4.3:编辑配置文件
[root@ldap-master (11:31:23)/etc/openldap]# cat slapd.ldif
#
# See slapd-config(5) for details on configuration options.
# This file should NOT be world readable.
#
dn: cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcPidFile: /var/run/openldap/slapd.pid
#
# TLS settings
#
olcTLSCACertificatePath: /etc/openldap/certs
olcTLSCertificateFile: "OpenLDAP Server"
olcTLSCertificateKeyFile: /etc/openldap/certs/password
#
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#
#olcReferral: ldap://root.openldap.org
#
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 64-bit encryption for simple bind
#
#olcSecurity: ssf=1 update_ssf=112 simple_bind=64
#
# Load dynamic backend modules:
# - modulepath is architecture dependent value (32/64-bit system)
# - back_sql.la backend requires openldap-servers-sql package
# - dyngroup.la and dynlist.la cannot be used at the same time
#
#dn: cn=module,cn=config
#objectClass: olcModuleList
#cn: module
#olcModulepath: /usr/lib/openldap
#olcModulepath: /usr/lib64/openldap
#olcModuleload: accesslog.la
#olcModuleload: auditlog.la
#olcModuleload: back_dnssrv.la
#olcModuleload: back_ldap.la
#olcModuleload: back_mdb.la
#olcModuleload: back_meta.la
#olcModuleload: back_null.la
#olcModuleload: back_passwd.la
#olcModuleload: back_relay.la
#olcModuleload: back_shell.la
#olcModuleload: back_sock.la
#olcModuleload: collect.la
#olcModuleload: constraint.la
#olcModuleload: dds.la
#olcModuleload: deref.la
#olcModuleload: dyngroup.la
#olcModuleload: dynlist.la
#olcModuleload: memberof.la
#olcModuleload: pcache.la
#olcModuleload: ppolicy.la
#olcModuleload: refint.la
#olcModuleload: retcode.la
#olcModuleload: rwm.la
#olcModuleload: seqmod.la
#olcModuleload: smbk5pwd.la
#olcModuleload: sssvlv.la
#olcModuleload: syncprov.la
#olcModuleload: translucent.la
#olcModuleload: unique.la
#olcModuleload: valsort.la
#
# Schema settings
#
dn: cn=schema,cn=config
objectClass: olcSchemaConfig
cn: schema
include: file:///etc/openldap/schema/core.ldif #将/etc/openldap/schema/目录下以ldif为结尾的模块都添加进来
include: file:///etc/openldap/schema/collective.ldif
include: file:///etc/openldap/schema/corba.ldif
include: file:///etc/openldap/schema/cosine.ldif
include: file:///etc/openldap/schema/duaconf.ldif
include: file:///etc/openldap/schema/dyngroup.ldif
include: file:///etc/openldap/schema/inetorgperson.ldif
include: file:///etc/openldap/schema/java.ldif
include: file:///etc/openldap/schema/misc.ldif
include: file:///etc/openldap/schema/nis.ldif
include: file:///etc/openldap/schema/openldap.ldif
include: file:///etc/openldap/schema/ppolicy.ldif
include: file:///etc/openldap/schema/pmi.ldif
include: file:///etc/openldap/schema/samba.ldif
include: file:///etc/openldap/schema/freeradius.ldif
#
# Frontend settings
#
dn: olcDatabase=frontend,cn=config
objectClass: olcDatabaseConfig
objectClass: olcFrontendConfig
olcDatabase: frontend
#
# Sample global access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
#
#olcAccess: to dn.base="" by * read
#olcAccess: to dn.base="cn=Subschema" by * read
#olcAccess: to *
# by self write
# by users read
# by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#
#
# Configuration database
#
dn: olcDatabase=config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: config
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c
n=auth" manage by * none
#
# Server status monitoring
#
dn: olcDatabase=monitor,cn=config
objectClass: olcDatabaseConfig
olcDatabase: monitor
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c
n=auth" read by dn.base="cn=acadmin,dc=test,dc=net,dc=cn" read by * none #这里把cn为管理员名称,dc为域名
#
# Backend database definitions
#
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: hdb
olcSuffix: dc=test,dc=net,dc=cn #这里要和上面的cn和dc一样
olcRootDN: cn=acadmin,dc=test,dc=net,dc=cn #还有这里同上
olcRootPW: {SSHA}hnxiKpbSXyzF1sazYma5FBlkdD39dpU6 #加上刚才设置的密码
olcDbDirectory: /var/lib/ldap
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
简单说一下这里的cn和dc, cn相当于名字,dc相当与域名,有几级域名就写几个dc。
这里slapd.ldif的初始文件就配置完成了。
2.4.4:设置数据库
[root@ldap-master (11:31:54)/etc/openldap]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@ldap-master (11:36:40)/etc/openldap]# chown -R ldap:ldap /var/lib/ldap
数据库这里就简单了,直接拷贝过来加上权限即可。
2.4.5:使用slapd.ldif初始化配置文件
这里如果导入错误,请检查slapd.ldif文件内容,注意每行后面不能有空格。
检查完后,删除slapd.d文件夹内的文件重新执行导入命令。
[root@ldap-master (11:43:16)/etc/openldap]# slapadd -n 0 -F slapd.d -l slapd.ldif
_#################### 100.00% eta none elapsed none fast!
Closing DB...
[root@ldap-master (11:43:18)/etc/openldap]# chown -R ldap:ldap slapd.d
2.4.6:启动服务
如果这里启动失败,请检查上面关于文件夹权限的设置。
[root@ldap-master (11:45:35)/etc/openldap]# systemctl start slapd
[root@ldap-master (11:45:41)/etc/openldap]# systemctl enable slapd
Created symlink from /etc/systemd/system/multi-user.target.wants/slapd.service to /usr/lib/systemd/system/slapd.service.
使用LDAP Admin软件来测试ldap服务
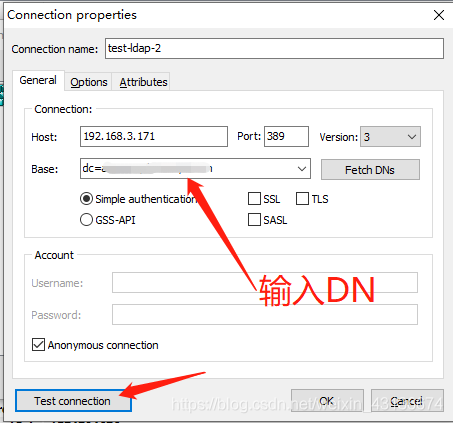
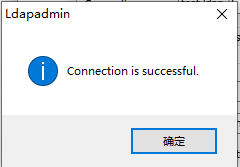
2.4.7:开启日志功能
创建日志存放目录,并授权给ldap用户。
[root@ldap-master (14:54:54)/etc/openldap]# mkdir /var/log/slapd
[root@ldap-master (14:55:04)/etc/openldap]# touch /var/log/slapd/slapd.log
[root@ldap-master (14:55:15)/etc/openldap]# chown -R ldap:ldap /var/log/slapd
在/etc/rsyslog.conf的74行添加如下内容:
74 local4.* /var/log/slapd/slapd.log
设置日志切割(因为日志存放越久,日志文件占用的空间就越大,开启日志切割,只保留最近的日志)
root@ldap-master (15:02:55)/etc/openldap]# vim /etc/logrotate.d/slapd
/var/log/slapd/slapd.log{
daily #每天轮询一次
rotate 5 #保存5个历史日志文件,超过的删除
copytruncate #复制源日志内容后,清空文件,而不是创建新文件
dateext #切割文件时,文件名带有日期
missingok #如果指定的目录不存在,会报错,此选项用来抑制报错
}
测试日志切割功能
[root@ldap-master (15:06:59)/etc/openldap]# ll /var/log/slapd/
total 0
-rw-r--r-- 1 ldap ldap 0 Nov 26 14:55 slapd.log
[root@ldap-master (15:07:11)/etc/openldap]# logrotate -f /etc/logrotate.d/slapd
[root@ldap-master (15:07:49)/etc/openldap]# ll /var/log/slapd/
total 0
-rw-r--r-- 1 ldap ldap 0 Nov 26 15:07 slapd.log
-rw-r--r-- 1 ldap ldap 0 Nov 26 15:07 slapd.log-20191126
重新编辑slapd.ldif,添加支持日志功能的模块。
在配置文件的第10行下面,紧跟一行添加如下内容,注意不要有空格。
[root@ldap-master (11:45:47)/etc/openldap]# vim slapd.ldif
11 olcLogLevel: stats
这里有人会说,为什么不用ldif文件热添加呢,因为我们是新建的ldap服务,直接使用初始化文件去配置,以后出现问题就可以把配置文件copy走,在另一个服务器上继续开启服务而不丢配置。
然后重新生成配置文件,来测试是否生成日志。
这里我们创建一个初始化用的脚本,为后面一步步添加功能做下简化,
[root@ldap-master (15:12:48)/etc/openldap]# vim config_init.sh
[root@ldap-master (15:17:23)/etc/openldap]# chmod +x config_init.sh
#!/bin/bash
rm -rf slapd.d/*
slapadd -n 0 -F slapd.d -l slapd.ldif
chown -R ldap:ldap slapd.d
systemctl restart slapd
[root@ldap-master (15:17:35)/etc/openldap]#
测试日志功能
[root@ldap-master (15:18:04)/etc/openldap]# sh config_init.sh
_#################### 100.00% eta none elapsed none fast!
Closing DB...
[root@ldap-master (15:19:02)/etc/openldap]# systemctl restart rsyslog
[root@ldap-master (15:19:27)/etc/openldap]# systemctl restart slapd
[root@ldap-master (15:19:38)/etc/openldap]# cat /var/log/slapd/slapd.log
Nov 26 15:19:38 ldap-master slapd[19478]: daemon: shutdown requested and initiated.
Nov 26 15:19:38 ldap-master slapd[19478]: slapd shutdown: waiting for 0 operations/tasks to finish
Nov 26 15:19:38 ldap-master slapd[19478]: slapd stopped.
Nov 26 15:19:38 ldap-master slapd[19533]: @(#) $OpenLDAP: slapd 2.4.44 (Jan 29 2019 17:42:45) $#012#011mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
Nov 26 15:19:38 ldap-master slapd[19535]: slapd starting
[root@ldap-master (15:19:39)/etc/openldap]#
2.5:安装phpldapadmin管理软件
该软件可以在web上对ldap进行管理,有中文的,方便一些。
2.5.1:安装所需依赖包
yum -y install epel-release
yum -y install phpldapadmin
2.5.2:编辑/etc/httpd/conf.d/phpldapadmin.conf用来允许所有网段访问:
vim /etc/httpd/conf.d/phpldapadmin.conf
<VirtualHost *:80>
ServerName openldap.test.net.cn
Alias /phpldapadmin /usr/share/phpldapadmin/htdocs
Alias /ldapadmin /usr/share/phpldapadmin/htdocs
<Directory /usr/share/phpldapadmin/htdocs>
<IfModule mod_authz_core.c>
# Apache 2.4
Require all granted
Require local
</IfModule>
<IfModule !mod_authz_core.c>
# Apache 2.2
Order Deny,Allow
Deny from all
Allow from 127.0.0.1
Allow from ::1
</IfModule>
</Directory>
</VirtualHost>
2.5.3:修改 /etc/phpldapadmin/config.php文件,将397行取消注释,并注释398行,用来开启使用dn登录。
[root@ldap-master (15:23:49)/etc/openldap]# vim /etc/phpldapadmin/config.php
397 $servers->setValue('login','attr','dn');
398 // $servers->setValue('login','attr','uid');
编辑httpd的配置文件,在96行添加ServerName localhost:80
[root@ldap-master (15:26:10)/etc/openldap]# vim /etc/httpd/conf/httpd.conf
96 ServerName localhost:80
开启http服务,查看phpldapadmin是否可登录
[root@ldap-master (15:29:07)/etc/openldap]# systemctl start httpd
[root@ldap-master (15:29:16)/etc/openldap]# systemctl enable httpd
Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service.
2.5.4:在主机的hosts文件中添加一条解析记录
192.168.2.147 openldap.test.net.cn
2.5.5:测试登录
访问http://IP/ldapadmin/


这里我们看见没有任何信息,这是因为我们还没有初始化域。
2.5.6:取消phpldapadmin警告信息
在初始化域之前,我们修改一下phpldapadmin的警告信息,取消掉警告。
修改 /etc/phpldapadmin/config.php的第166行为如下内容
[root@ldap-master (15:29:21)/etc/openldap]# vim /etc/phpldapadmin/config.php
166 $config->custom->appearance['hide_template_warning'] = true;
03:加固LDAP(ssl和https)
我们先不初始化域,先把ldap变得更安全一下–添加tls(这里是内网使用,所以用的是自签的证书,这个证书不要设置密码!否则ldap会不识别证书)
2.1:ldap配置ssl
这里我们使用自己的CA服务器
CA服务器:
[root@CA (15:41:08)~]# yum -y install openssl #1.安装CA服务器
[root@CA (15:42:04)~]# cd /etc/pki/CA/
[root@CA (15:42:06)/etc/pki/CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) #2.生成CA服务器自己的私钥
Generating RSA private key, 2048 bit long modulus
....................+++
..................+++
e is 65537 (0x10001)
[root@CA (15:42:15)/etc/pki/CA]#
[root@CA (15:42:15)/etc/pki/CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 #3.生成自签名证书
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN #国家
State or Province Name (full name) []:BeiJing #省份
Locality Name (eg, city) [Default City]:BeiJing #城市
Organization Name (eg, company) [Default Company Ltd]:test.net.cn #域名
Organizational Unit Name (eg, section) []:internet #类型
Common Name (eg, your name or your server's hostname) []:ca.test.net.cn #填写ca服务器的域名
Email Address []:
[root@CA (15:44:01)/etc/pki/CA]#
[root@CA (15:44:01)/etc/pki/CA]# echo "ca.test.net.cn" >> /etc/hostname #补一下主机名
[root@CA (15:46:11)/etc/pki/CA]# hostname
CA
[root@CA (15:46:17)/etc/pki/CA]# cat /etc/hostname
CA
ca.test.net.cn
[root@CA (15:46:25)/etc/pki/CA]#
[root@CA (15:46:25)/etc/pki/CA]# touch index.txt
[root@CA (15:46:49)/etc/pki/CA]# echo 01 >serial
[root@CA (15:47:19)/etc/pki/CA]# tree
.
├── cacert.pem
├── certs
├── crl
├── index.txt
├── newcerts
├── private
│ └── cakey.pem
└── serial
4 directories, 4 files
LDAP服务器:
[root@ldap-master (15:34:48)/etc/openldap]# cd /etc/openldap/certs/
[root@ldap-master (15:50:13)/etc/openldap/certs]# (umask 077;openssl genrsa -out openldapkey147.pem 2048) #生成LDAP服务器的私钥
Generating RSA private key, 2048 bit long modulus
..................................+++
.....................................................................................................+++
e is 65537 (0x10001)
[root@ldap-master (15:50:26)/etc/openldap/certs]# openssl req -new -key openldapkey147.pem -out openldap147.csr -days 3650 -subj "/C=CN/ST=BeiJing/L=BeiJing/O=test.net.cn/OU=internet/CN=192.168.2.147"
# 使用私钥生成申请CA证书的文件 这里的CN指的是本机ip
[root@ldap-master (15:50:56)/etc/openldap/certs]# scp openldap147.csr root@192.168.2.148:/root #使用scp将申请文件传送到CA服务器
The authenticity of host '192.168.2.148 (192.168.2.148)' can't be established.
ECDSA key fingerprint is SHA256:qE6NS65QCbFIKWl80AiHPtYYZE8aH3PctGvUpMSLzaA.
ECDSA key fingerprint is MD5:13:74:3e:e1:49:1c:4c:9d:08:d4:eb:b5:e8:92:e7:a1.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.2.148' (ECDSA) to the list of known hosts.
root@192.168.2.148's password:
Permission denied, please try again.
root@192.168.2.148's password:
Permission denied, please try again.
root@192.168.2.148's password:
openldap147.csr 100% 1021 114.2KB/s 00:00
CA服务器:
[root@CA (15:53:44)/etc/pki/CA]# openssl ca -in /root/openldap147.csr -out /etc/pki/CA/certs/openldapcert147.crt -days 3650 #同意ldap的证书,并下发证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Nov 26 07:53:50 2019 GMT
Not After : Nov 23 07:53:50 2029 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
organizationName = test.net.cn
organizationalUnitName = internet
commonName = 192.168.2.147
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
1A:9B:B1:28:A7:57:F7:28:CE:69:F6:C5:07:4B:E2:D2:5E:6F:A4:95
X509v3 Authority Key Identifier:
keyid:AA:5C:0E:BC:87:05:14:5B:DC:23:9D:74:5B:E1:23:B9:05:E1:71:A9
Certificate is to be certified until Nov 23 07:53:50 2029 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@CA (15:53:54)/etc/pki/CA]# tree
.
├── cacert.pem
├── certs
│ └── openldapcert147.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│ └── 01.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old
4 directories, 9 files
[root@CA (15:54:31)/etc/pki/CA]# scp cacert.pem certs/openldapcert147.crt root@192.168.2.147:/root #使用scp将证书和验证文件传到ldap服务器中
The authenticity of host '192.168.2.147 (192.168.2.147)' can't be established.
ECDSA key fingerprint is SHA256:4pvEkT1xlxD1JbHjJQBRyMOEmoiPfh51jKOJpgZn/3U.
ECDSA key fingerprint is MD5:12:f9:57:f8:40:ac:d9:4b:ab:6c:1c:10:f8:ed:2b:59.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.2.147' (ECDSA) to the list of known hosts.
root@192.168.2.147's password:
cacert.pem 100% 1367 1.3MB/s 00:00
openldapcert147.crt 100% 4528 2.6MB/s 00:00
LDAP 服务器:
[root@ldap-master (15:53:08)/etc/openldap/certs]# cd
[root@ldap-master (15:56:34)~]# ls
anaconda-ks.cfg cacert.pem init.sh openldapcert147.crt
[root@ldap-master (15:56:34)~]# cp openldapcert147.crt cacert.pem /etc/openldap/certs/ #ldap服务器将这两个文件导入到证书存放目录,并赋予目录权限
[root@ldap-master (15:56:48)~]# chown -R ldap.ldap /etc/openldap/certs
[root@ldap-master (15:56:58)~]# chmod -R 0400 /etc/openldap/certs/openldap*
[root@ldap-master (15:57:05)~]# chmod -R 0400 /etc/openldap/certs/cacert.pem
编辑ldap的配置文件slapd.ldif
指明证书文件的路径和验证级别
[root@ldap-master (16:19:19)/etc/openldap]# vim slapd.ldif
15 olcTLSCACertificateFile: /etc/openldap/certs/cacert.pem
16 olcTLSCertificateFile: /etc/openldap/certs/openldapcert130.crt
17 olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey130.pem
18 olcTLSVerifyClient: never
在slapd的配置文件中修改模式:添加ldaps:///
[root@ldap-master (14:07:20)/etc/openldap]# vim /etc/sysconfig/slapd
9 SLAPD_URLS="ldapi:/// ldap:/// ldaps:///"
将ldap.conf文本修改成如下内容:
#
# LDAP Defaults
#
# See ldap.conf(5) for details
# This file should be world readable but not world writable.
BASE dc=test,dc=net,dc=cn
#URI ldap://ldap.example.com ldap://ldap-master.example.com:666
URI ldaps://192.168.2.147
#SIZELIMIT 12
#TIMELIMIT 15
#DEREF never
TLS_REQCERT hard
#TLS_CACERTDIR /etc/openldap/certs
TLS_CACERT /etc/openldap/certs/cacert.pem
# Turning this off breaks GSSAPI used with krb5 when rdns = false
SASL_NOCANON on
重启服务
[root@ldap-master (14:08:31)/etc/openldap]# systemctl restart slapd
[root@ldap-master (14:09:58)/etc/openldap]# ss -tunlp | grep 636
tcp LISTEN 0 128 *:22 *:* users:(("sshd",pid=6366,fd=3))
tcp LISTEN 0 128 *:636 *:* users:(("slapd",pid=7237,fd=10))
tcp LISTEN 0 128 :::80 :::* users:(("httpd",pid=6504,fd=4),("httpd",pid=6503,fd=4),("httpd",pid=6501,fd=4),("httpd",pid=6500,fd=4),("httpd",pid=6498,fd=4),("httpd",pid=6367,fd=4))
tcp LISTEN 0 128 :::22 :::* users:(("sshd",pid=6366,fd=4))
tcp LISTEN 0 128 :::636 :::* users:(("slapd",pid=7237,fd=11))
再次使用ldapadmin软件来测试

这里使用ldapadmin测试ssl的时候,会提示证书无效等提示,这里我们把ca的根证书(cacert.pem,在ca服务器上)导入到本地就可以了。
导入方法:使用Google浏览器,打开设置–>高级–>证书管理–>受信任的根证书–>导入–>选择所有文件–>选择cacert.pem–>导入成功
2.2:http配置https
ldap-master:
[root@ldap-master (14:14:25)~]# mkdir /etc/httpd/certs
[root@ldap-master (14:14:34)~]# cd /etc/httpd/certs/
[root@ldap-master (14:14:39)/etc/httpd/certs]# (umask 077;openssl genrsa -out openldapadmin.key 2048)
Generating RSA private key, 2048 bit long modulus
...............................................................+++
....................................................................................................................+++
e is 65537 (0x10001)
[root@ldap-master (14:14:49)/etc/httpd/certs]# openssl req -new -key openldapadmin.key -out openldapadmin.csr -days 3650 -subj "/C=CN/ST=BeiJing/L=BeiJing/O=test.net.cn/OU=Internet/CN=openldap.test.net.cn"
[root@ldap-master (14:15:01)/etc/httpd/certs]# scp openldapadmin.csr root@192.168.6.143:/root
The authenticity of host '192.168.6.143 (192.168.6.143)' can't be established.
ECDSA key fingerprint is SHA256:OCxk4wtcCVaYZR+NKD3xrJSgQwUAwT2WeTQ69JGhmjM.
ECDSA key fingerprint is MD5:88:57:6d:72:36:6f:58:1c:36:84:8a:19:91:54:5b:d0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.6.143' (ECDSA) to the list of known hosts.
root@192.168.6.143's password:
openldapadmin.csr 100% 1037 1.2MB/s 00:00
[root@ldap-master (14:15:25)/etc/httpd/certs]#
CA:
[root@ca (14:19:25)/etc/pki/CA]# openssl ca -in /root/openldapadmin.csr -out /etc/pki/CA/certs/openldapadmin.crt -days 3650
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Dec 2 06:19:56 2019 GMT
Not After : Nov 29 06:19:56 2029 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
organizationName = test.net.cn
organizationalUnitName = Internet
commonName = openldap.test.net.cn
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
CD:8A:3F:06:B8:FA:DC:E1:FE:A4:0D:81:D3:66:21:95:47:E5:32:AC
X509v3 Authority Key Identifier:
keyid:B5:68:D1:D2:61:0B:13:E1:4B:6D:C2:2A:AE:31:39:97:72:F5:80:B9
Certificate is to be certified until Nov 29 06:19:56 2029 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@ca (14:19:59)/etc/pki/CA]# scp /etc/pki/CA/certs/openldapadmin.crt root@192.168.2.147:/root
The authenticity of host '192.168.2.147 (192.168.2.147)' can't be established.
ECDSA key fingerprint is SHA256:4pvEkT1xlxD1JbHjJQBRyMOEmoiPfh51jKOJpgZn/3U.
ECDSA key fingerprint is MD5:12:f9:57:f8:40:ac:d9:4b:ab:6c:1c:10:f8:ed:2b:59.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.2.147' (ECDSA) to the list of known hosts.
root@192.168.2.147's password:
openldapadmin.crt 100% 4550 2.9MB/s 00:00
[root@ca (14:20:25)/etc/pki/CA]#
ldap
[root@ldap-master (14:15:25)/etc/httpd/certs]# cp /root/openldapadmin.crt ./
[root@ldap-master (14:22:08)/etc/httpd/certs]# chown -R apache:apache /etc/httpd/certs
[root@ldap-master (14:22:14)/etc/httpd/certs]# chmod -R 0400 /etc/httpd/certs/*
[root@ldap-master (14:22:21)/etc/httpd/certs]# yum -y install mod_ssl
编辑phpldapadmin.conf配置文件
[root@ldap-master (14:23:50)/etc/httpd/certs]# vim /etc/httpd/conf.d/phpldapadmin.conf
1 #
2 # Web-based tool for managing LDAP servers
3 #
4 <VirtualHost *:443>
5 ServerName openldap.test.net.cn
6 DocumentRoot "/usr/share/phpldapadmin/htdocs"
7 SSLEngine on
8 SSLCertificateFile "/etc/httpd/certs/openldapadmin.crt"
9 SSLCertificateKeyFile "/etc/httpd/certs/openldapadmin.key"
10 Alias /phpldapadmin /usr/share/phpldapadmin/htdocs
11 Alias /ldapadmin /usr/share/phpldapadmin/htdocs
12
13 <Directory /usr/share/phpldapadmin/htdocs>
14 <IfModule mod_authz_core.c>
15 # Apache 2.4
16 Require all granted
17 Require local
18 </IfModule>
19 <IfModule !mod_authz_core.c>
20 # Apache 2.2
21 Order Deny,Allow
22 Deny from all
23 Allow from 127.0.0.1
24 Allow from ::1
25 </IfModule>
26 </Directory>
27 </VirtualHost>
重启服务并查看443端口
[root@ldap-master (14:25:20)/etc/httpd/certs]# systemctl restart httpd
[root@ldap-master (14:25:38)/etc/httpd/certs]# ss -tunlp | grep 443
tcp LISTEN 0 128 :::443 :::* users:(("httpd",pid=7421,fd=6),("httpd",pid=7420,fd=6),("httpd",pid=7419,fd=6),("httpd",pid=7418,fd=6),("httpd",pid=7417,fd=6),("httpd",pid=7416,fd=6))
[root@ldap-master (14:25:47)/etc/httpd/certs]#

点击不安全,点击证书
04:LDAP的ACL
4.1:设置ACL
这个是注释一下添加的ACL意思,可能会多出空格,如果想要直接复制文本,请使用下面的文件。
可复制的slapd.ldif
#
# See slapd-config(5) for details on configuration options.
# This file should NOT be world readable.
#
dn: cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcPidFile: /var/run/openldap/slapd.pid
olcLogLevel: stats
olcDisallows: bind_anon ##关闭匿名访问
#
# TLS settings
#
olcTLSCACertificateFile: /etc/openldap/certs/cacert.pem
olcTLSCertificateFile: /etc/openldap/certs/openldapcert130.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey130.pem
olcTLSVerifyClient: never
#
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#
#olcReferral: ldap://root.openldap.org
#
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 64-bit encryption for simple bind
#
#olcSecurity: ssf=1 update_ssf=112 simple_bind=64
#
# Load dynamic backend modules:
# - modulepath is architecture dependent value (32/64-bit system)
# - back_sql.la backend requires openldap-servers-sql package
# - dyngroup.la and dynlist.la cannot be used at the same time
#
#dn: cn=module,cn=config
#objectClass: olcModuleList
#cn: module
#olcModulepath: /usr/lib/openldap
#olcModulepath: /usr/lib64/openldap
#olcModuleload: accesslog.la
#olcModuleload: auditlog.la
#olcModuleload: back_dnssrv.la
#olcModuleload: back_ldap.la
#olcModuleload: back_mdb.la
#olcModuleload: back_meta.la
#olcModuleload: back_null.la
#olcModuleload: back_passwd.la
#olcModuleload: back_relay.la
#olcModuleload: back_shell.la
#olcModuleload: back_sock.la
#olcModuleload: collect.la
#olcModuleload: constraint.la
#olcModuleload: dds.la
#olcModuleload: deref.la
#olcModuleload: dyngroup.la
#olcModuleload: dynlist.la
#olcModuleload: memberof.la
#olcModuleload: pcache.la
#olcModuleload: ppolicy.la
#olcModuleload: refint.la
#olcModuleload: retcode.la
#olcModuleload: rwm.la
#olcModuleload: seqmod.la
#olcModuleload: smbk5pwd.la
#olcModuleload: sssvlv.la
#olcModuleload: syncprov.la
#olcModuleload: translucent.la
#olcModuleload: unique.la
#olcModuleload: valsort.la
#
# Schema settings
#
dn: cn=schema,cn=config
objectClass: olcSchemaConfig
cn: schema
include: file:///etc/openldap/schema/core.ldif
include: file:///etc/openldap/schema/collective.ldif
include: file:///etc/openldap/schema/corba.ldif
include: file:///etc/openldap/schema/cosine.ldif
include: file:///etc/openldap/schema/duaconf.ldif
include: file:///etc/openldap/schema/dyngroup.ldif
include: file:///etc/openldap/schema/inetorgperson.ldif
include: file:///etc/openldap/schema/java.ldif
include: file:///etc/openldap/schema/misc.ldif
include: file:///etc/openldap/schema/nis.ldif
include: file:///etc/openldap/schema/openldap.ldif
include: file:///etc/openldap/schema/ppolicy.ldif
include: file:///etc/openldap/schema/pmi.ldif
include: file:///etc/openldap/schema/samba.ldif
include: file:///etc/openldap/schema/freeradius.ldif
#
# Frontend settings
#
dn: olcDatabase=frontend,cn=config
objectClass: olcDatabaseConfig
objectClass: olcFrontendConfig
olcDatabase: frontend
olcAccess: to attrs=userPassword.shadowLastChange ##开启用户可以修改密码
by dn.children="ou=Admin,dc=test,dc=net,dc=cn" write
by anonymous auth
by * none
olcAccess: to dn.subtree="dc=test,dc=net,dc=cn" ##设置同步用户、搜索用户、可读,设置ldapadmin管理组
by dn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn" read
by dn="cn=clientsearch,ou=Admin,dc=test,dc=net,dc=cn" read
by group.exact="cn=ldapadmin,ou=Admin,dc=test,dc=net,dc=cn" write
by users read
olcAccess: to dn.subtree="" #设置可以读取schema
by * read
#
# Sample global access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
#
#olcAccess: to dn.base="" by * read
#olcAccess: to dn.base="cn=Subschema" by * read
#olcAccess: to *
# by self write
# by users read
# by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#
#
# Configuration database
#
dn: olcDatabase=config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: config
olcAccess: to *
by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by group.exact="cn=configadmin,ou=Admin,dc=test,dc=net,dc=cn" write #设置一个配置管理员
by * none
#
# Server status monitoring
#
dn: olcDatabase=monitor,cn=config
objectClass: olcDatabaseConfig
olcDatabase: monitor
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c
n=auth" read by dn.base="cn=acadmin,dc=test,dc=net,dc=cn" read by * none
#
# Backend database definitions
#
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: hdb
olcSuffix: dc=test,dc=net,dc=cn
olcRootDN: cn=acadmin,dc=test,dc=net,dc=cn
olcRootPW: {SSHA}hnxiKpbSXyzF1sazYma5FBlkdD39dpU6
olcDbDirectory: /var/lib/ldap
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
4.2:验证ACL
先创建一个基本域
vim /usr/share/migrationtools/migrate_common.ph
......
$DEFAULT_MAIL_DOMAIN = "test.net.cn"; #改为我们的域名
# Default base
$DEFAULT_BASE = "dc=test,dc=net,dc=cn"; #改为我们的域名
......
$EXTENDED_SCHEMA = 1; #改为1
生成基本域
[root@ldap-master (15:24:08)/etc/openldap]# /usr/share/migrationtools/migrate_base.pl > /etc/openldap/basedomin.ldif
然后我们简化一下这个基本域里的内容
dn: dc=test,dc=net,dc=cn
dc: test
objectClass: top
objectClass: domain
objectClass: domainRelatedObject
associatedDomain: test.net.cn
dn: ou=Admin,dc=test,dc=net,dc=cn
objectClass: top
objectClass: organizationalUnit
ou: Admin
dn: ou=People,dc=test,dc=net,dc=cn
ou: People
objectClass: top
objectClass: organizationalUnit
objectClass: domainRelatedObject
associatedDomain: test.net.cn
dn: ou=Group,dc=test,dc=net,dc=cn
ou: Group
objectClass: top
objectClass: organizationalUnit
objectClass: domainRelatedObject
associatedDomain: test.net.cn
再生成几个基本账户
[root@ldap-master (15:53:06)/etc/openldap]# useradd test1
[root@ldap-master (15:53:31)/etc/openldap]# useradd test2
[root@ldap-master (15:53:34)/etc/openldap]# tail -2 /etc/passwd
test1:x:1000:1000::/home/test1:/bin/bash
test2:x:1001:1001::/home/test2:/bin/bash
[root@ldap-master (15:53:42)/etc/openldap]# tail -2 /etc/passwd > testuser
[root@ldap-master (15:53:54)/etc/openldap]# tail -2 /etc/group
test1:x:1000:
test2:x:1001:
[root@ldap-master (15:54:04)/etc/openldap]# tail -2 /etc/group > testgroup
[root@ldap-master (15:54:12)/etc/openldap]# /usr/share/migrationtools/migrate_passwd.pl testuser > testuser.ldif
[root@ldap-master (15:55:49)/etc/openldap]# cat testuser.ldif
dn: uid=test1,ou=People,dc=test,dc=net,dc=cn
uid: test1
cn: test1
sn: test1
mail: test1@test.net.cn
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: 123456
shadowLastChange: 18232
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1000
gidNumber: 1000
homeDirectory: /home/test1
dn: uid=test2,ou=People,dc=test,dc=net,dc=cn
uid: test2
cn: test2
sn: test2
mail: test2@test.net.cn
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: 123456
shadowLastChange: 18232
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1001
gidNumber: 1001
homeDirectory: /home/test2
[root@ldap-master (15:55:55)/etc/openldap]# /usr/share/migrationtools/migrate_group.pl testgroup > testgroup.ldif
[root@ldap-master (15:56:22)/etc/openldap]# cat testgroup.ldif
dn: cn=test1,ou=Group,dc=test,dc=net,dc=cn
objectClass: posixGroup
objectClass: top
cn: test1
userPassword: {crypt}x
gidNumber: 1000
dn: cn=test2,ou=Group,dc=test,dc=net,dc=cn
objectClass: posixGroup
objectClass: top
cn: test2
userPassword: {crypt}x
gidNumber: 1001
[root@ldap-master (15:56:29)/etc/openldap]#
然后将导入基本域的ldif配置添加到初始化脚本中。
#!/bin/bash
rm -rf slapd.d/*
slapadd -n 0 -F slapd.d -l slapd.ldif
chown -R ldap:ldap slapd.d
systemctl restart slapd
ldapadd -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -w 123456 -f basedomin.ldif
ldapadd -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -w 123456 -f testuser.ldif
ldapadd -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -w 123456 -f testgroup.ldif
然后执行初始化脚本
[root@ldap-master (16:15:52)/etc/openldap]# sh config_init.sh
_#################### 100.00% eta none elapsed none fast!
Closing DB...
adding new entry "dc=test,dc=net,dc=cn"
adding new entry "ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "ou=People,dc=test,dc=net,dc=cn"
adding new entry "ou=Group,dc=test,dc=net,dc=cn"
adding new entry "uid=test1,ou=People,dc=test,dc=net,dc=cn"
adding new entry "uid=test2,ou=People,dc=test,dc=net,dc=cn"
adding new entry "cn=test1,ou=Group,dc=test,dc=net,dc=cn"
adding new entry "cn=test2,ou=Group,dc=test,dc=net,dc=cn"
然后登陆ldapadmin软件,就能看见我们的基本用户了。

然后使用ldif文件,创建出configadmin,ldapadmin,syncuser1,clientsearch几个用户和属性。
[root@ldap-master (16:44:26)/etc/openldap]# cat ldapadmin.ldif
dn: cn=ldapadmin,ou=Admin,dc=test,dc=net,dc=cn
cn: ldapadmin
objectClass: groupOfNames
member: uid=test1,ou=People,dc=test,dc=net,dc=cn
dn: cn=configadmin,ou=Admin,dc=test,dc=net,dc=cn
cn: configadmin
objectClass: groupOfNames
member: uid=test2,ou=People,dc=test,dc=net,dc=cn
dn: cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn
uid: syncuser1
cn: syncuser1
sn: syncuser1
mail: syncuser1@test.net.cn
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: 123456
loginShell: /bin/bash
uidNumber: 6666
gidNumber: 0
homeDirectory: /home/syncuser1
dn: cn=clientsearch,ou=Admin,dc=test,dc=net,dc=cn
uid: clientsearch
cn: clientsearch
sn: clientsearch
mail: clientsearch@test.net.cn
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: 123456
loginShell: /bin/bash
uidNumber: 7777
gidNumber: 0
homeDirectory: /home/clientsearch
执行脚本,导入这些用户
[root@ldap-master (16:42:25)/etc/openldap]# ldapadd -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -w 123456 -f ldapadmin.ldif
adding new entry "cn=ldapadmin,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=configadmin,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=clientsearch,ou=Admin,dc=test,dc=net,dc=cn"
创建一个普通用户并导入
[root@ldap-master (16:50:00)/etc/openldap]# ldapadd -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -w 123456 -f ljuser.ldif
adding new entry "cn=lj2,ou=People,dc=test,dc=net,dc=cn"
[root@ldap-master (16:50:21)/etc/openldap]# cat ljuser.ldif
dn: cn=lj2,ou=People,dc=test,dc=net,dc=cn
uid: lj2
cn: lj2
sn: lj2
mail: lj2@test.net.cn
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: 123456
shadowLastChange: 18232
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1006
gidNumber: 0
homeDirectory: /home/lj2
创建一个测试用的ldif
[root@ldap-master (16:53:14)/etc/openldap]# cat testgroup2.ldif
dn: cn=testgroup2,ou=Group,dc=test,dc=net,dc=cn
objectClass: top
objectClass: posixGroup
gidNumber: 10086
cn: testgroup2
开始测试:
| 用户 | 权限 |
|---|---|
| lj2 | 普通用户 |
| test1 | ldap管理员 |
| test2 | ldap配置管理员 |
4.2.1:使用普通用户测试
提示无写权限。
[root@ldap-master (16:54:58)/etc/openldap]# ldapadd -x -D "cn=lj2,ou=People,dc=test,dc=net,dc=cn" -w 123456 -f testgroup2.ldif
adding new entry "cn=testgroup2,ou=Group,dc=test,dc=net,dc=cn"
ldap_add: Insufficient access (50)
additional info: no write access to parent
4.2.2:使用ldap管理员进行导入
成功导入。
[root@ldap-master (17:02:32)/etc/openldap]# ldapadd -x -D "uid=test1,ou=People,dc=test,dc=net,dc=cn" -w 123456 -f testgroup2.ldif
adding new entry "cn=testgroup2,ou=Group,dc=test,dc=net,dc=cn"
4.2.3:测试匿名访问

4.2.4:使用普通用户修改配置
提示无权限修改。
[root@ldap-master (17:14:56)/etc/openldap]# ldapadd -x -D "cn=lj2,ou=people,dc=test,dc=net,dc=cn" -w 123456 -f testlog.ldif
modifying entry "cn=config"
ldap_modify: Insufficient access (50)
4.2.5:使用配置管理员修改配置
没有错误提示。
[root@ldap-master (17:15:09)/etc/openldap]# ldapadd -x -D "uid=test2,ou=people,dc=test,dc=net,dc=cn" -w 123456 -f testlog.ldif
modifying entry "cn=config"
查看配置文件可以看到,日志级别已经修改为any。
[root@ldap-master (17:16:56)/etc/openldap]# cat slapd.d/cn\=config.ldif
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 8bf1493d
dn: cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcDisallows: bind_anon
olcPidFile: /var/run/openldap/slapd.pid
olcTLSCACertificateFile: /etc/openldap/certs/cacert.pem
olcTLSCertificateFile: /etc/openldap/certs/openldapcert130.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey130.pem
olcTLSVerifyClient: never
structuralObjectClass: olcGlobal
entryUUID: b45d4cce-a927-1039-9d2e-4dc306d98512
creatorsName: cn=config
createTimestamp: 20191202081554Z
olcLogLevel: any
entryCSN: 20191202091656.412168Z#000000#000#000000
modifiersName: uid=test2,ou=People,dc=test,dc=net,dc=cn
modifyTimestamp: 20191202091656Z
05:ldap的高可用
5.1:环境准备
在ldap-slave上,配置和ldap-mstar一样的配置。 这里使用了CA服务器的http服务当配置文件的中转站。
#1.初始化系统环境
#2.安装软件
yum -y install openldap openldap-servers openldap-clients compat-openldap openldap-devel migrationtools samba* freeradius*
#3.初始化配置文件
cd /etc/openldap
mv slapd.d{,.bak}
mkdir slapd.d
#密码:
ldap_passwd="{SSHA}hnxiKpbSXyzF1sazYma5FBlkdD39dpU6"
#默认为123456,可使用slappasswd来生成新的密码。
#下载主配置文件
wget -c http://192.168.2.148/init/slapd.ldif
wget -c http://192.168.2.148/init/config_init.sh
chmod u+x config_init
#4.拷贝schema文件
cp /usr/share/doc/freeradius-3.0.13/schemas/ldap/openldap/freeradius.ldif /etc/openldap/schema/
cp /usr/share/doc/freeradius-3.0.13/schemas/ldap/openldap/freeradius.schema /etc/openldap/schema/
cp /usr/share/doc/samba-4.9.1/LDAP/samba.schema /etc/openldap/schema/
cp /usr/share/doc/samba-4.9.1/LDAP/samba.ldif /etc/openldap/schema/
#5.拷贝数据库文件
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
chown -R ldap:ldap /var/lib/ldap
#6.配置日志模块
mkdir /var/log/slapd
touch /var/log/slapd/slapd.log
chown -R ldap:ldap /var/log/slapd
rm -f /etc/rsyslog.conf
wget http://192.168.2.148:/init/rsyslog.conf .
mv rsyslog.conf /etc/
cd /etc/logrotate.d/
wget http://192.168.2.148:/init/slapd
#7.安装phpldapadmin
yum -y install epel-release
yum -y install phpldapadmin
cd /etc/httpd/conf.d/
rm -f phpldapadmin.conf
wget http://192.168.2.148:/init/phpldapadmin.conf
cd /etc/phpldapadmin/
rm -f config.php
wget http://192.168.2.148:/init/config.php
#http的证书
cd /etc/httpd/
mkdir certs
wget http://192.168.2.148:/init/http_ca/openldapadmin.key
wget http://192.168.2.148:/init/http_ca/openldapadmin.csr
wget http://192.168.2.148:/init/http_ca/openldapadmin.crt
chmod 0400 openldapadmin.*
chown -R apache:apache /etc/httpd/certs
yum -y install mod_ssl
#openldap的证书
cd /etc/openldap/certs/
(umask 077;openssl genrsa -out openldapkey150.pem 2048)
openssl req -new -key openldapkey150.pem -out openldap150.csr -days 3650 -subj "/C=CN/ST=BeiJing/L=BeiJing/O=test.net.cn/OU=internet/CN=192.168.2.150"
scp openldap150.csr root@192.168.2.148:/root
#CA服务器的操作
cd /etc/pki/CA/
openssl ca -in /root/openldap150.csr -out /etc/pki/CA/certs/openldapcert150.crt -days 3650
scp cacert.pem certs/openldapcert150.crt root@192.168.2.150:/root
#ldap-slave的操作
cd /root
cp openldapcert150.crt cacert.pem /etc/openldap/certs/
chown -R ldap.ldap /etc/openldap/certs
chmod -R 0400 /etc/openldap/certs/openldap*
chmod -R 0400 /etc/openldap/certs/cacert.pem
#修改slapd.ldif的文件
olcTLSCACertificateFile: /etc/openldap/certs/cacert.pem
olcTLSCertificateFile: /etc/openldap/certs/openldapcert150.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey150.pem
#重新生成配置文件
cd /etc/openldap/
sh config_init.sh
vim /etc/sysconfig/slapd
SLAPD_URLS="ldapi:/// ldap:/// ldaps:///"
#修改ldap.conf文件
###############
#
# LDAP Defaults
#
# See ldap.conf(5) for details
# This file should be world readable but not world writable.
BASE dc=test,dc=net,dc=cn
#URI ldap://ldap.example.com ldap://ldap-master.example.com:666
URI ldaps://192.168.2.150
#SIZELIMIT 12
#TIMELIMIT 15
#DEREF never
TLS_REQCERT hard
#TLS_CACERTDIR /etc/openldap/certs
TLS_CACERT /etc/openldap/certs/cacert.pem
# Turning this off breaks GSSAPI used with krb5 when rdns = false
SASL_NOCANON on
################
#开启服务自启
systemctl enable httpd
systemctl enable slapd
5.2:验证环境

由此可见,我们的环境基本配置相同了,只有条目方面还没有配置。
5.3:开始配置主从同步
1.更新时间
这一步在初始化中就已经做完了
2.主机名互相解析
将ip地址和主机名添加到/etc/hosts文件中(两台机器都要操作)
192.168.2.147 ldap-master.test.net.cn
192.168.2.150 ldap-slave.test.net.cn
3.使两个节点的数据一致。
主节点导出用户
[root@ldap-master (20:06:24)~]# ldapsearch -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -W -b "dc=test,dc=net,dc=cn" -LLL -H ldaps://192.168.2.147 > ldapdata.ldif
Enter LDAP Password: 123456
[root@ldap-master (20:06:53)~]# scp ldapdata.ldif root@192.168.2.150:/root
The authenticity of host '192.168.2.150 (192.168.2.150)' can't be established.
ECDSA key fingerprint is SHA256:mM1dhjEqAsS+/GK7cnG1C6v72+gp/APGUCgnDopZWws.
ECDSA key fingerprint is MD5:bd:fc:1d:7d:ef:bc:1d:09:ba:0f:9b:88:f1:41:89:f9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.2.150' (ECDSA) to the list of known hosts.
root@192.168.2.150's password:
ldapdata.ldif 100% 3346 2.1MB/s 00:00
[root@ldap-master (20:07:13)~]#
LDAP-slave导入用户
[root@ldap-slave (20:08:27)~]# ldapadd -x -W -D "cn=acadmin,dc=test,dc=net,dc=cn" -f ldapdata.ldif
Enter LDAP Password:
adding new entry "dc=test,dc=net,dc=cn"
adding new entry "ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "ou=People,dc=test,dc=net,dc=cn"
adding new entry "ou=Group,dc=test,dc=net,dc=cn"
adding new entry "uid=test1,ou=People,dc=test,dc=net,dc=cn"
adding new entry "uid=test2,ou=People,dc=test,dc=net,dc=cn"
adding new entry "cn=test1,ou=Group,dc=test,dc=net,dc=cn"
adding new entry "cn=test2,ou=Group,dc=test,dc=net,dc=cn"
adding new entry "cn=ldapadmin,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=configadmin,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=clientsearch,ou=Admin,dc=test,dc=net,dc=cn"
adding new entry "cn=lj2,ou=People,dc=test,dc=net,dc=cn"
adding new entry "cn=testgroup2,ou=Group,dc=test,dc=net,dc=cn"


5.4:打开同步模块
编辑/etc/openldap/slapd.ldif文件取消41、42、43、45、72行的注释
41 dn: cn=module,cn=config
42 objectClass: olcModuleList
43 cn: module
44 #olcModulepath: /usr/lib/openldap
45 olcModulepath: /usr/lib64/openldap
46 #olcModuleload: accesslog.la
......
72 olcModuleload: syncprov.la
5.5:配置一个开启主机节点设置的ldif文件。
[root@ldap-master (22:29:17)~]# cat sync_master.ldif
# config syncprov
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpCheckpoint: 100 10
olcSpSessionLog: 100
# add index
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcDbIndex
olcDbIndex: entryCSN,entryUUID eq
5.6:使用sync_master.ldif开启主节点设置
[root@ldap-master (22:28:30)~]# ldapadd -Y EXTERNAL -H ldapi:/// -f sync_master.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "olcOverlay=syncprov,olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
5.7:从节点设置
同样创建一个sync_slave.ldif
[root@ldap-slave (22:43:12)~]# cat sync_slave.ldif
# config syncprov
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
# add index
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcDbIndex
olcDbIndex: entryCSN,entryUUID eq
-
add: olcSyncRepl
olcSyncRepl: rid=002 #复制ID,每一个节点需要保持唯一ID
provider=ldaps://192.168.2.147:636/ #主节点地址
bindmethod=simple #简单认证模式
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn" #同步使用的账户,如果面不同步,请看这里,可能是uid和cn的问题。
credentials=123456 #同步账户的密码
searchbase="dc=test,dc=net,dc=cn" #搜索的基本路径
scope=sub #=subtree,包含自身及子子孙孙的条目
schemachecking=on #校验schema
type=refreshAndPersist # 持续同步,如果同步出现问题,下次同步不会重新同步,会接着上次的任务同步
retry="5 5 300 +" #尝试时间,5分钟尝试一次,尝试5次后,每隔300秒重试一次
attrs="*,+" #同步所有属性
interval=00:00:00:10 #每隔10s同步一次
可复制文本
# config syncprov
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
# add index
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcDbIndex
olcDbIndex: entryCSN,entryUUID eq
-
add: olcSyncRepl
olcSyncRepl: rid=002
provider=ldaps://192.168.2.147:636/
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials=123456
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
使用sync_slave.ldif去开启从节点的同步
[root@ldap-slave (22:43:06)~]# ldapadd -Y EXTERNAL -H ldapi:/// -f sync_slave.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "olcOverlay=syncprov,olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
5.8:创建sync_group来测试主从同步


(可选)5.8.1:配置镜像模式
master:
在slapd.ldif文件最下面追加
olcDbIndex: entryCSN,entryUUID eq
olcMirrorMode: on
olcSyncRepl: rid=001
provider=ldaps://192.168.2.150:636/ #有条件的可以设置为域名
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials="123456"
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpCheckpoint: 100 10
olcSpSessionLog: 100
slave
olcDbIndex: entryCSN,entryUUID eq
olcMirrorMode: on
olcSyncRepl: rid=002
provider=ldaps://192.168.2.147:636/
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials="123456"
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpCheckpoint: 100 10
olcSpSessionLog: 100
(可选)5.8.2:配置双主模式
这里需要设置为域名访问,上面签发证书时使用的是ip地址,可以重新生成域名的证书,或更改ldap.conf里面的客户端验证模式为never
[root@ldap-slave (01:01:18)/etc/openldap]# cat ldap.conf
#
# LDAP Defaults
#
# See ldap.conf(5) for details
# This file should be world readable but not world writable.
BASE dc=test,dc=net,dc=cn
#URI ldap://ldap.example.com ldap://ldap-master.example.com:666
URI ldaps://192.168.2.150
#SIZELIMIT 12
#TIMELIMIT 15
#DEREF never
TLS_REQCERT never
TLS_CACERT /etc/openldap/certs/cacert.pem
# Turning this off breaks GSSAPI used with krb5 when rdns = false
SASL_NOCANON on
master-1
#
# See slapd-config(5) for details on configuration options.
# This file should NOT be world readable.
#
dn: cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcPidFile: /var/run/openldap/slapd.pid
olcLogLevel: stats
olcDisallows: bind_anon
#
# TLS settings
#
olcTLSCACertificateFile: /etc/openldap/certs/cacert.pem
olcTLSCertificateFile: /etc/openldap/certs/openldapcert147.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey147.pem
olcTLSVerifyClient: never
olcServerID: 1 ldaps://ldap-master.test.net.cn
olcServerID: 2 ldaps://ldap-slave.test.net.cn
#
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#
#olcReferral: ldap://root.openldap.org
#
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 64-bit encryption for simple bind
#
#olcSecurity: ssf=1 update_ssf=112 simple_bind=64
#
# Load dynamic backend modules:
# - modulepath is architecture dependent value (32/64-bit system)
# - back_sql.la backend requires openldap-servers-sql package
# - dyngroup.la and dynlist.la cannot be used at the same time
#
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
#olcModulepath: /usr/lib/openldap
olcModulepath: /usr/lib64/openldap
#olcModuleload: accesslog.la
#olcModuleload: auditlog.la
#olcModuleload: back_dnssrv.la
#olcModuleload: back_ldap.la
#olcModuleload: back_mdb.la
#olcModuleload: back_meta.la
#olcModuleload: back_null.la
#olcModuleload: back_passwd.la
#olcModuleload: back_relay.la
#olcModuleload: back_shell.la
#olcModuleload: back_sock.la
#olcModuleload: collect.la
#olcModuleload: constraint.la
#olcModuleload: dds.la
#olcModuleload: deref.la
#olcModuleload: dyngroup.la
#olcModuleload: dynlist.la
#olcModuleload: memberof.la
#olcModuleload: pcache.la
#olcModuleload: ppolicy.la
#olcModuleload: refint.la
#olcModuleload: retcode.la
#olcModuleload: rwm.la
#olcModuleload: seqmod.la
#olcModuleload: smbk5pwd.la
#olcModuleload: sssvlv.la
olcModuleload: syncprov.la
#olcModuleload: translucent.la
#olcModuleload: unique.la
#olcModuleload: valsort.la
#
# Schema settings
#
dn: cn=schema,cn=config
objectClass: olcSchemaConfig
cn: schema
include: file:///etc/openldap/schema/core.ldif
include: file:///etc/openldap/schema/collective.ldif
include: file:///etc/openldap/schema/corba.ldif
include: file:///etc/openldap/schema/cosine.ldif
include: file:///etc/openldap/schema/duaconf.ldif
include: file:///etc/openldap/schema/dyngroup.ldif
include: file:///etc/openldap/schema/inetorgperson.ldif
include: file:///etc/openldap/schema/java.ldif
include: file:///etc/openldap/schema/misc.ldif
include: file:///etc/openldap/schema/nis.ldif
include: file:///etc/openldap/schema/openldap.ldif
include: file:///etc/openldap/schema/ppolicy.ldif
include: file:///etc/openldap/schema/pmi.ldif
include: file:///etc/openldap/schema/samba.ldif
include: file:///etc/openldap/schema/freeradius.ldif
#
# Frontend settings
#
dn: olcDatabase=frontend,cn=config
objectClass: olcDatabaseConfig
objectClass: olcFrontendConfig
olcDatabase: frontend
olcAccess: to attrs=userPassword,shadowLastChange
by dn.children="ou=Admin,dc=test,dc=net,dc=cn" write
by anonymous auth
by self write
by * none
olcAccess: to dn.subtree="dc=test,dc=net,dc=cn"
by dn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn" read
by dn="cn=clientsearch,ou=Admin,dc=test,dc=net,dc=cn" read
by group.exact="cn=ldapadmin,ou=Admin,dc=test,dc=net,dc=cn" write
by users read
olcAccess: to dn.subtree=""
by * read
#
# Sample global access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
#
#olcAccess: to dn.base="" by * read
#olcAccess: to dn.base="cn=Subschema" by * read
#olcAccess: to *
# by self write
# by users read
# by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#
#
# Configuration database
#
dn: olcDatabase=config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: config
olcAccess: to *
by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by group.exact="cn=configadmin,ou=Admin,dc=test,dc=net,dc=cn" write
by * none
#
# Server status monitoring
#
dn: olcDatabase=monitor,cn=config
objectClass: olcDatabaseConfig
olcDatabase: monitor
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c
n=auth" read by dn.base="cn=acadmin,dc=test,dc=net,dc=cn" read by * none
#
# Backend database definitions
#
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: hdb
olcSuffix: dc=test,dc=net,dc=cn
olcRootDN: cn=acadmin,dc=test,dc=net,dc=cn
olcRootPW: {SSHA}hnxiKpbSXyzF1sazYma5FBlkdD39dpU6
olcDbDirectory: /var/lib/ldap
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
olcDbIndex: entryCSN,entryUUID eq
olcMirrorMode: on
olcSyncRepl: rid=001
provider=ldaps://192.168.2.147:636/
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials="123456"
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
olcSyncRepl: rid=002
provider=ldaps://192.168.2.150:636/
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials="123456"
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpCheckpoint: 100 10
olcSpSessionLog: 100
master-2
#
# See slapd-config(5) for details on configuration options.
# This file should NOT be world readable.
#
dn: cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcPidFile: /var/run/openldap/slapd.pid
olcLogLevel: stats
olcDisallows: bind_anon
#
# TLS settings
#
olcTLSCACertificateFile: /etc/openldap/certs/cacert.pem
olcTLSCertificateFile: /etc/openldap/certs/openldapcert150.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey150.pem
olcTLSVerifyClient: never
olcServerID: 1 ldaps://ldap-master.test.net.cn
olcServerID: 2 ldaps://ldap-slave.test.net.cn
#
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#
#olcReferral: ldap://root.openldap.org
#
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 64-bit encryption for simple bind
#
#olcSecurity: ssf=1 update_ssf=112 simple_bind=64
#
# Load dynamic backend modules:
# - modulepath is architecture dependent value (32/64-bit system)
# - back_sql.la backend requires openldap-servers-sql package
# - dyngroup.la and dynlist.la cannot be used at the same time
#
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
#olcModulepath: /usr/lib/openldap
olcModulepath: /usr/lib64/openldap
#olcModuleload: accesslog.la
#olcModuleload: auditlog.la
#olcModuleload: back_dnssrv.la
#olcModuleload: back_ldap.la
#olcModuleload: back_mdb.la
#olcModuleload: back_meta.la
#olcModuleload: back_null.la
#olcModuleload: back_passwd.la
#olcModuleload: back_relay.la
#olcModuleload: back_shell.la
#olcModuleload: back_sock.la
#olcModuleload: collect.la
#olcModuleload: constraint.la
#olcModuleload: dds.la
#olcModuleload: deref.la
#olcModuleload: dyngroup.la
#olcModuleload: dynlist.la
#olcModuleload: memberof.la
#olcModuleload: pcache.la
#olcModuleload: ppolicy.la
#olcModuleload: refint.la
#olcModuleload: retcode.la
#olcModuleload: rwm.la
#olcModuleload: seqmod.la
#olcModuleload: smbk5pwd.la
#olcModuleload: sssvlv.la
olcModuleload: syncprov.la
#olcModuleload: translucent.la
#olcModuleload: unique.la
#olcModuleload: valsort.la
#
# Schema settings
#
dn: cn=schema,cn=config
objectClass: olcSchemaConfig
cn: schema
include: file:///etc/openldap/schema/core.ldif
include: file:///etc/openldap/schema/collective.ldif
include: file:///etc/openldap/schema/corba.ldif
include: file:///etc/openldap/schema/cosine.ldif
include: file:///etc/openldap/schema/duaconf.ldif
include: file:///etc/openldap/schema/dyngroup.ldif
include: file:///etc/openldap/schema/inetorgperson.ldif
include: file:///etc/openldap/schema/java.ldif
include: file:///etc/openldap/schema/misc.ldif
include: file:///etc/openldap/schema/nis.ldif
include: file:///etc/openldap/schema/openldap.ldif
include: file:///etc/openldap/schema/ppolicy.ldif
include: file:///etc/openldap/schema/pmi.ldif
include: file:///etc/openldap/schema/samba.ldif
include: file:///etc/openldap/schema/freeradius.ldif
#
# Frontend settings
#
dn: olcDatabase=frontend,cn=config
objectClass: olcDatabaseConfig
objectClass: olcFrontendConfig
olcDatabase: frontend
olcAccess: to attrs=userPassword,shadowLastChange
by dn.children="ou=Admin,dc=test,dc=net,dc=cn" write
by anonymous auth
by self write
by * none
olcAccess: to dn.subtree="dc=test,dc=net,dc=cn"
by dn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn" read
by dn="cn=clientsearch,ou=Admin,dc=test,dc=net,dc=cn" read
by group.exact="cn=ldapadmin,ou=Admin,dc=test,dc=net,dc=cn" write
by users read
olcAccess: to dn.subtree=""
by * read
#
# Sample global access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
#
#olcAccess: to dn.base="" by * read
#olcAccess: to dn.base="cn=Subschema" by * read
#olcAccess: to *
# by self write
# by users read
# by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#
#
# Configuration database
#
dn: olcDatabase=config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: config
olcAccess: to *
by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by group.exact="cn=configadmin,ou=Admin,dc=test,dc=net,dc=cn" write
by * none
#
# Server status monitoring
#
dn: olcDatabase=monitor,cn=config
objectClass: olcDatabaseConfig
olcDatabase: monitor
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c
n=auth" read by dn.base="cn=acadmin,dc=test,dc=net,dc=cn" read by * none
#
# Backend database definitions
#
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: hdb
olcSuffix: dc=test,dc=net,dc=cn
olcRootDN: cn=acadmin,dc=test,dc=net,dc=cn
olcRootPW: {SSHA}hnxiKpbSXyzF1sazYma5FBlkdD39dpU6
olcDbDirectory: /var/lib/ldap
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
olcDbIndex: entryCSN,entryUUID eq
olcMirrorMode: on
olcSyncRepl: rid=001
provider=ldaps://ldap-master.test.net.cn:636/
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials="123456"
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
olcSyncRepl: rid=002
provider=ldaps://ldap-slave.test.net.cn:636/
bindmethod=simple
binddn="cn=syncuser1,ou=Admin,dc=test,dc=net,dc=cn"
credentials="123456"
searchbase="dc=test,dc=net,dc=cn"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="5 5 300 +"
attrs="*,+"
interval=00:00:00:10
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpCheckpoint: 100 10
olcSpSessionLog: 100
5.9:配置KeepAlived高可用
5.9.1:安装keepalived。
[root@ldap-master (18:51:24)~]# yum -y install keepalived
[root@ldap-slave (18:51:25)~]# yum -y install keepalived
5.9.2:证书设置
由于我们要设置一个vip地址(250),为了让访问ldap的服务感知不到ldap的切换,我们要把访问ldap服务的程序中ldap的地址改为这个vip地址,所以在客户端申请证书时,就会出现问题(因为我们之前的证书是147和150的证书)。所以,我们需要把ldap的证书认证模式改为never模式,实现即使证书不能认证,还会使用https加密通信。但是为了让客户端使证书有效,我们需要使用vip地址(250)的证书。
5.9.3:备份之前的证书
ldap-master:
[root@ldap-master (18:55:51)~]# cd /etc/openldap/certs/
[root@ldap-master (19:04:21)/etc/openldap/certs]#
[root@ldap-master (19:04:21)/etc/openldap/certs]# ls
cacert.pem key3.db openldapcert147.crt password
cert8.db openldap147.csr openldapkey147.pem secmod.db
[root@ldap-master (19:04:22)/etc/openldap/certs]# mkdir cert147
[root@ldap-master (19:04:33)/etc/openldap/certs]# ls
cacert.pem cert8.db openldap147.csr openldapkey147.pem secmod.db
cert147 key3.db openldapcert147.crt password
[root@ldap-master (19:04:34)/etc/openldap/certs]# mv openldap* cert147/
[root@ldap-master (19:05:13)/etc/openldap/certs]# ls
cacert.pem cert147 cert8.db key3.db password secmod.db
5.9.4:重新生成新的证书
ldap-master
[root@ldap-master (19:05:14)/etc/openldap/certs]# (umask 077;openssl genrsa -out openldapkey250.pem 2048)
Generating RSA private key, 2048 bit long modulus
....+++
....+++
e is 65537 (0x10001)
[root@ldap-master (19:09:49)/etc/openldap/certs]# openssl req -new -key openldapkey250.pem -out openldap250.csr -days 3650 -subj "/C=CN/ST=BeiJing/L=BeiJing/O=test.net.cn/OU=internet/CN=192.168.2.250"
[root@ldap-master (19:10:08)/etc/openldap/certs]# scp openldap250.csr root@192.168.2.148:/root
root@192.168.2.148's password:
openldap250.csr 100% 1021 830.6KB/s 00:00
CA服务器
[root@CA (18:59:01)~]# cd /etc/pki/CA
[root@CA (19:11:28)/etc/pki/CA]# openssl ca -in /root/openldap250.csr -out /etc/pki/CA/certs/openldapcert250.crt -days 3650
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4 (0x4)
Validity
Not Before: Dec 14 11:11:52 2019 GMT
Not After : Dec 11 11:11:52 2029 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
organizationName = test.net.cn
organizationalUnitName = internet
commonName = 192.168.2.250
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
1E:54:A8:73:58:01:6D:70:B4:15:A1:2B:00:D9:32:EC:F3:44:42:5B
X509v3 Authority Key Identifier:
keyid:B5:68:D1:D2:61:0B:13:E1:4B:6D:C2:2A:AE:31:39:97:72:F5:80:B9
Certificate is to be certified until Dec 11 11:11:52 2029 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@CA (19:11:56)/etc/pki/CA]#
[root@CA (19:11:56)/etc/pki/CA]# scp certs/openldapcert250.crt root@192.168.2.147:/root
root@192.168.2.147's password:
openldapcert250.crt 100% 4528 2.6MB/s 00:00
ldap-master
[root@ldap-master (19:11:00)/etc/openldap/certs]# cp /root/openldap
openldapadmin.crt openldapcert130.crt openldapcert147.crt openldapcert250.crt
[root@ldap-master (19:11:00)/etc/openldap/certs]# cp /root/openldapcert250.crt ./
[root@ldap-master (19:14:11)/etc/openldap/certs]# ls
cacert.pem cert8.db openldap250.csr openldapkey250.pem secmod.db
cert147 key3.db openldapcert250.crt password
[root@ldap-master (19:14:16)/etc/openldap/certs]# chown -R ldap.ldap /etc/openldap/certs
[root@ldap-master (19:14:35)/etc/openldap/certs]# chmod -R 0400 /etc/openldap/certs/openldap*
[root@ldap-master (19:14:42)/etc/openldap/certs]#
生成证书后,重新编辑slapd.ldif,修改证书文件的名称
olcTLSCertificateFile: /etc/openldap/certs/openldapcert250.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey250.pem
重新生成配置文件
[root@ldap-master (19:24:30)/etc/openldap]# sh config_init.sh
_#################### 100.00% eta none elapsed none fast!
Closing DB...
ldap-slave证书设置
直接使用slapd-master的证书就可以
传输之前先备份
先备份原来的证书
ldap-slave
[root@ldap-slave (18:56:14)~]# cd /etc/openldap/certs/
[root@ldap-slave (19:07:20)/etc/openldap/certs]# ls
cacert.pem key3.db openldapcert150.crt password
cert8.db openldap150.csr openldapkey150.pem secmod.db
[root@ldap-slave (19:07:21)/etc/openldap/certs]# mkdir certs150
[root@ldap-slave (19:07:31)/etc/openldap/certs]# mv openldap* certs150/
[root@ldap-slave (19:07:39)/etc/openldap/certs]# ls
cacert.pem cert8.db certs150 key3.db password secmod.db
[root@ldap-slave (19:07:42)/etc/openldap/certs]#
ldap-master
[root@ldap-master (19:18:55)/etc/openldap/certs]# scp openldap* root@192.168.2.150:/etc/openldap/certs/
root@192.168.2.150's password:
openldap250.csr 100% 1021 925.5KB/s 00:00
openldapcert250.crt 100% 4528 3.1MB/s 00:00
openldapkey250.pem 100% 1675 736.4KB/s 00:00
ldap-slave
这时就可以使用ldap-master申请的证书了。
[root@ldap-slave (19:07:42)/etc/openldap/certs]# ls
cacert.pem certs150 openldap250.csr openldapkey250.pem secmod.db
cert8.db key3.db openldapcert250.crt password
[root@ldap-slave (19:21:28)/etc/openldap/certs]# chown -R ldap.ldap /etc/openldap/certs
然后同样需要修改一下slapd.ldif文件中证书的名称
[root@ldap-slave (19:21:54)/etc/openldap/certs]# grep 250 ../slapd.ldif
olcTLSCertificateFile: /etc/openldap/certs/openldapcert250.crt
olcTLSCertificateKeyFile: /etc/openldap/certs/openldapkey250.pem
也需要重新生成配置文件
[root@ldap-slave (19:26:25)/etc/openldap]# sh config_init.sh
_#################### 100.00% eta none elapsed none fast!
Closing DB...
[root@ldap-slave (19:26:27)/etc/openldap]#
测试证书

这时会显示证书有问题

测试ldap-slave。

此时两个ldap节点的证书都已经设置好了,接下来我们就需要设置keepalived了。
5.9.5:设置keepalived。
ldap-master
备份原来的keepalived.conf,并生成新的keepalived.conf配置文件。
[root@ldap-master (20:03:30)/etc/keepalived]# mv keepalived.conf{,.bak}
[root@ldap-master (20:08:47)/etc/keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
}
#notification_email_from Alexandre.Cassen@firewall.loc
#smtp_server 192.168.200.1
#smtp_connect_timeout 30
router_id ldapA
vrrp_skip_check_adv_addr
#vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_script check_ldap_server_status {
script "/etc/keepalived/check-ldap-server.sh"
interval 3
weight -5
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.2.250
}
notify_master "/etc/keepalived/to_master.sh"
notify_backup "/etc/keepalived/to_master.sh"
notify_stop "/etc/keepalived/to_stop.sh"
track_script {
check_ldap_server_status
}
}
里面的脚本
[root@ldap-master (20:13:02)/etc/keepalived]# cat check-ldap-server.sh
#!/bin/bash
ldapPid=$(ps -ef |grep slapd|grep -v grep|awk '{print $2}' |grep -v PID)
if [ "$ldapPid" == "" ]; then
systemctl stop keepalived
echo "slapd stop"
exit 1
else
exit 0
fi
[root@ldap-master (20:15:03)/etc/keepalived]# cat to_master.sh
#!/bin/bash
systemctl start slapd
[root@ldap-master (20:15:10)/etc/keepalived]# cat to_stop.sh
#!/bin/bash
systemctl stop slapd
[root@ldap-master (20:15:14)/etc/keepalived]#
添加可执行权限
[root@ldap-master (20:15:14)/etc/keepalived]# ls
check-ldap-server.sh keepalived.conf keepalived.conf.bak to_master.sh to_stop.sh
[root@ldap-master (20:16:05)/etc/keepalived]# chmod +x to_* check-ldap-server.sh
[root@ldap-master (20:16:30)/etc/keepalived]# ll
total 20
-rwxr-xr-x 1 root root 193 Dec 14 20:12 check-ldap-server.sh
-rw-r--r-- 1 root root 954 Dec 14 20:08 keepalived.conf
-rw-r--r-- 1 root root 3598 Aug 13 04:37 keepalived.conf.bak
-rwxr-xr-x 1 root root 34 Dec 14 20:12 to_master.sh
-rwxr-xr-x 1 root root 33 Dec 14 20:13 to_stop.sh
[root@ldap-master (20:16:31)/etc/keepalived]#
将脚本文件复制到ldap-slave中
[root@ldap-master (20:16:31)/etc/keepalived]# scp check-ldap-server.sh to_* root@192.168.2.150:/etc/keepalived/
root@192.168.2.150's password:
check-ldap-server.sh 100% 193 163.7KB/s 00:00
to_master.sh 100% 34 21.3KB/s 00:00
to_stop.sh 100% 33 24.4KB/s 00:00
[root@ldap-master (20:17:31)/etc/keepalived]#
ldap-slave
[root@ldap-slave (20:10:40)/etc/keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
}
#notification_email_from Alexandre.Cassen@firewall.loc
#smtp_server 192.168.200.1
#smtp_connect_timeout 30
router_id ldapB
vrrp_skip_check_adv_addr
#vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_script check_ldap_server_status {
script "/etc/keepalived/check-ldap-server.sh"
interval 3
weight -5
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
priority 98
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.2.250
}
notify_master "/etc/keepalived/to_master.sh"
notify_backup "/etc/keepalived/to_master.sh"
notify_stop "/etc/keepalived/to_stop.sh"
track_script {
check_ldap_server_status
}
}
[root@ldap-slave (20:18:47)/etc/keepalived]# ls
check-ldap-server.sh keepalived.conf keepalived.conf.bak to_master.sh to_stop.sh
[root@ldap-slave (20:18:49)/etc/keepalived]#
启动keepalived
[root@ldap-master (20:18:41)/etc/keepalived]# systemctl start keepalived
[root@ldap-master (20:20:53)/etc/keepalived]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:e8:05:aa brd ff:ff:ff:ff:ff:ff
inet 192.168.2.147/24 brd 192.168.2.255 scope global dynamic eth0
valid_lft 1610sec preferred_lft 1610sec
inet 192.168.2.250/32 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fee8:5aa/64 scope link
valid_lft forever preferred_lft forever
设置为开机自启动。
[root@ldap-master (20:20:56)/etc/keepalived]# systemctl enable keepalived
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
[root@ldap-slave (20:46:03)/etc/keepalived]# systemctl enable keepalived
Created symlink from /etc/systemd/system/multi-user.target.wants/keepalived.service to /usr/lib/systemd/system/keepalived.service.
ldap-slave
[root@ldap-slave (20:18:49)/etc/keepalived]# systemctl start keepalived
[root@ldap-slave (20:25:14)/etc/keepalived]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:77:ca:56 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.150/24 brd 192.168.2.255 scope global dynamic eth0
valid_lft 1462sec preferred_lft 1462sec
inet6 fe80::20c:29ff:fe77:ca56/64 scope link
valid_lft forever preferred_lft forever
测试
ldap-master主机停止slapd服务,可以看见250地址消失了。
[root@ldap-master (20:21:31)/etc/keepalived]# systemctl stop slapd
[root@ldap-master (20:25:55)/etc/keepalived]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:e8:05:aa brd ff:ff:ff:ff:ff:ff
inet 192.168.2.147/24 brd 192.168.2.255 scope global dynamic eth0
valid_lft 1308sec preferred_lft 1308sec
inet6 fe80::20c:29ff:fee8:5aa/64 scope link
valid_lft forever preferred_lft forever
[root@ldap-master (20:25:58)/etc/keepalived]#
此时keepalived已经自己停止了
[root@ldap-master (20:25:58)/etc/keepalived]# systemctl status keepalived
● keepalived.service - LVS and VRRP High Availability Monitor
Loaded: loaded (/usr/lib/systemd/system/keepalived.service; enabled; vendor preset: disabled)
Active: inactive (dead) since Sat 2019-12-14 20:25:57 CST; 3min 5s ago
Main PID: 8342 (code=exited, status=0/SUCCESS)
CGroup: /system.slice/keepalived.service
Dec 14 20:21:00 ldap-master.test.net.cn Keepalived_vrrp[8344]: VRRP_Instance(VI_1) Sending...
Dec 14 20:21:00 ldap-master.test.net.cn Keepalived_vrrp[8344]: Sending gratuitous ARP on e...
Dec 14 20:21:00 ldap-master.test.net.cn Keepalived_vrrp[8344]: Sending gratuitous ARP on e...
Dec 14 20:21:00 ldap-master.test.net.cn Keepalived_vrrp[8344]: Sending gratuitous ARP on e...
Dec 14 20:21:00 ldap-master.test.net.cn Keepalived_vrrp[8344]: Sending gratuitous ARP on e...
Dec 14 20:25:56 ldap-master.test.net.cn Keepalived[8342]: Stopping
Dec 14 20:25:56 ldap-master.test.net.cn systemd[1]: Stopping LVS and VRRP High Availabil.....
Dec 14 20:25:56 ldap-master.test.net.cn Keepalived_vrrp[8344]: VRRP_Instance(VI_1) sent 0 ...
Dec 14 20:25:56 ldap-master.test.net.cn Keepalived_vrrp[8344]: VRRP_Instance(VI_1) removin...
Dec 14 20:25:57 ldap-master.test.net.cn systemd[1]: Stopped LVS and VRRP High Availabili...r.
Hint: Some lines were ellipsized, use -l to show in full.
[root@ldap-master (20:29:03)/etc/keepalived]#
同时查看ldap-slave主机
可以发现250地址漂移到ldap-slave主机上了。
[root@ldap-slave (20:26:01)/etc/keepalived]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:77:ca:56 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.150/24 brd 192.168.2.255 scope global dynamic eth0
valid_lft 1341sec preferred_lft 1341sec
inet 192.168.2.250/32 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe77:ca56/64 scope link
valid_lft forever preferred_lft forever
恢复主节点的keepalived
[root@ldap-master (20:29:03)/etc/keepalived]# systemctl start slapd
[root@ldap-master (20:30:55)/etc/keepalived]# systemctl start keepalived
[root@ldap-master (20:31:03)/etc/keepalived]# systemctl status keepalived
● keepalived.service - LVS and VRRP High Availability Monitor
Loaded: loaded (/usr/lib/systemd/system/keepalived.service; enabled; vendor preset: disabled)
Active: active (running) since Sat 2019-12-14 20:31:03 CST; 21s ago
Process: 9341 ExecStart=/usr/sbin/keepalived $KEEPALIVED_OPTIONS (code=exited, status=0/SUCCESS)
Main PID: 9342 (keepalived)
CGroup: /system.slice/keepalived.service
├─9342 /usr/sbin/keepalived -D
├─9343 /usr/sbin/keepalived -D
└─9344 /usr/sbin/keepalived -D
Dec 14 20:31:04 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:04 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:04 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:04 ldap-master.test.net.cn Keepalived_vrrp[9344]: Opening script file /etc/ke...
Dec 14 20:31:09 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:09 ldap-master.test.net.cn Keepalived_vrrp[9344]: VRRP_Instance(VI_1) Sending...
Dec 14 20:31:09 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:09 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:09 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Dec 14 20:31:09 ldap-master.test.net.cn Keepalived_vrrp[9344]: Sending gratuitous ARP on e...
Hint: Some lines were ellipsized, use -l to show in full.
可以看见250地址漂移回来了
[root@ldap-master (20:31:24)/etc/keepalived]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:e8:05:aa brd ff:ff:ff:ff:ff:ff
inet 192.168.2.147/24 brd 192.168.2.255 scope global dynamic eth0
valid_lft 1662sec preferred_lft 1662sec
inet 192.168.2.250/32 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fee8:5aa/64 scope link
valid_lft forever preferred_lft forever
ldap-slave节点上的250地址也消失了
[root@ldap-slave (20:27:42)/etc/keepalived]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:77:ca:56 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.150/24 brd 192.168.2.255 scope global dynamic eth0
valid_lft 1748sec preferred_lft 1748sec
inet6 fe80::20c:29ff:fe77:ca56/64 scope link
valid_lft forever preferred_lft forever
使用客户端测试

连接测试
连接250时并没有弹出证书提醒。

注意
如果节点出现问题,先启动slapd服务,再启动keepalived服务。
06:创建openLDAP的组织架构。
根据每个公司的组织架构去创建对应的openldap组织架构;
这里我们使用测试的组织架构

07:安装自助修改密码程序
我们使用的是开源的self-service-password程序。
(本篇文章内主机名和时间如果有偏差,请忽略这个问题。更换电脑原来的虚拟机没有了。。。)
这里我们只演示了一个节点的安装,另一个节点安装步骤相同,不再演示。
7.1:安装docker
[root@ldap-master (17:20:35)~]# wget -O /etc/yum.repos.d/docker-ce.repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
yum -y install docker-ce
[root@ldap-master (17:20:35)~]# systemctl start docker && systemctl enable docker
Created symlink from /etc/systemd/system/multi-user.target.wants/docker.service to /usr/lib/systemd/system/docker.service.
[root@ldap-radius-slave (17:20:55)~]#[root@ldap-master (17:20:35)~]#
7.2:编辑Dockerfile并构建镜像
[root@ldap-master (16:37:12)~]# cat Dockerfile
FROM php:7.3.10-apache-stretch
RUN apt update && apt install -y libldap2-dev && docker-php-ext-install ldap
RUN curl https://ltb-project.org/archives/ltb-project-self-service-password-1.3.tar.gz|tar zxf - -C /var/www/html --strip-components=1
[root@ldap-master (16:37:15)~]# docker build -t self-service-password:v0.1 .
7.3:部署镜像
部署镜像前我们需要把这个软件的配置文件导出来,然后加以修改,修改完成后放在我们本地目录,这样每次镜像出现问题的话,我们的配置文件也不会丢失。
这里就不演示导出的步骤了,这只放一下两个文件的代码
[root@ldap-radius-slave (17:24:20)~]# mkdir -pv /data/etc/self-service-password/conf/
mkdir: 已创建目录 "/data/etc"
mkdir: 已创建目录 "/data/etc/self-service-password"
mkdir: 已创建目录 "/data/etc/self-service-password/conf/"
[root@ldap-radius-master (16:40:46)/data/etc/self-service-password/conf]# ls
config.inc.local.php config.inc.php
config.inc.php 这个文件只是拿出来而已,并没有修改。
https://github.com/lichunpeng3300/openldap/wiki/config.inc.php
这个文件才是重点,我们需要仔细修改这个文件。
[root@ldap-radius-master (16:40:40)/data/etc/self-service-password/conf]# cat config.inc.local.php
<?php
# LDAP
$ldap_url = "ldap://10.10.4.240"; #ldap地址
$ldap_starttls = false; #是否使用tls加密,这里我尝试使用加密方式,但是失败了。。
$ldap_binddn = "cn=acadmin,dc=test,dc=net,dc=cn"; #可修改密码的管理员用户
$ldap_bindpw = "******"; #管理员的密码
$ldap_base = "dc=test,dc=net,dc=cn"; #根
$ldap_login_attribute = "uid";
$ldap_fullname_attribute = "cn";
$ldap_filter = "(&(objectClass=person)($ldap_login_attribute={login}))";
$hash = "ssha"; #密码加密方式
$keyphrase = "sdsg354[df(-4dsdfdfasdsvvsdsgfskkajfpaxcz/zcmai";
## Mail #这部分是通过邮件修改密码的配置
$mail_attribute = "mail";
$mail_address_use_ldap = false;
$mail_from = "ldap@test.net.cn"; #openldap管理员的邮箱
$mail_from_name = "重置密码"; #发送邮件时的主题
$mail_signature = "";
# Notify users anytime their password is changed
$notify_on_change = false;
# PHPMailer configuration (see https://github.com/PHPMailer/PHPMailer)
$mail_sendmailpath = '/usr/sbin/sendmail';
$mail_protocol = 'smtp';
$mail_smtp_debug = 0;
$mail_debug_format = 'error_log';
$mail_smtp_host = 'smtp.qiye.163.com'; #发送邮件的服务器
$mail_smtp_auth = true;
$mail_smtp_user = 'ldap@test.net.cn'; #openldap管理员的邮箱
$mail_smtp_pass = 'Qwer@3058'; #openldap管理员的密码
$mail_smtp_port = 25;
$mail_smtp_timeout = 30;
$mail_smtp_keepalive = false;
$mail_smtp_secure = 'tls';
$mail_smtp_autotls = true;
$mail_contenttype = 'text/plain';
$mail_wordwrap = 0;
$mail_charset = 'utf-8';
$mail_priority = 3;
$mail_newline = PHP_EOL;
[root@ldap-radius-master (16:48:40)/data/etc/self-service-password/conf]# docker run -p 8080:80 -v /data/etc/self-service-password/conf:/var/www/html/conf -d self-service-password:v0.1
然后查看docker镜像是否成功
[root@ldap-radius-master (16:48:40)/data/etc/self-service-password/conf]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
6c04864ce850 self-service-password:v0.1 "docker-php-entrypoi…" 3 hours ago Up 3 hours 0.0.0.0:8080->80/tcp frosty_beaver
然后访问http://192.168.0.250:8080(我们的vip地址,因为这里是搭建在ldap-master节点上的。)就可以了

这里我只保留两个功能,因为其他功能看起来并没有那么必要。一个知道原密码更改,一个不知道原密码更改,而且是使用的邮箱,既便宜又实惠啊!
7.4:测试高可用
因为我们两个节点都部署了更改密码的服务,这时我们关掉主节点的,测试一下副节点的更改密码服务。

08:设置用户密码加密策略
为了安全起见,所有人的密码必须是8位以上的。复杂度暂时不设置了。
8.1:打开ppolicy.la模块
编辑slapd.ldif
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulepath: /usr/lib64/openldap
...
olcModuleload: ppolicy.la #把这个模块的注释取消就可以了
...
然后在最下面添加定义的策略
dn: olcOverlay=ppolicy,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcPPolicyConfig
olcOverlay: ppolicy
olcPPolicyDefault: cn=default,ou=pwpolicies,dc=test,dc=net,dc=cn
olcPPolicyHashCleartext: TRUE #这个就是我们需要的属性,输入明文密码时,自动转换为ssha加密密码。
olcPPolicyUseLockout: TRUE
8.2:使用ldif文件将密码规则添加进去
[root@ldap-radius-master (17:15:07)/etc/openldap]# cat ppolicy.ldif
dn: ou=pwpolicies,dc=test,dc=net,dc=cn
objectClass: organizationalUnit
ou: pwpolicies
dn: cn=default,ou=pwpolicies,dc=test,dc=net,dc=cn
cn: default
objectClass: pwdPolicy
objectClass: person
pwdAllowUserChange: TRUE
pwdAttribute: userPassword
pwdExpireWarning: 259200
pwdFailureCountInterval: 0
pwdGraceAuthNLimit: 5
pwdInHistory: 5
pwdLockout: TRUE
pwdLockoutDuration: 300
pwdCheckQuality: 1
pwdMaxAge: 2592000
pwdMaxFailure: 5
pwdMinAge: 0
pwdMinLength: 8
pwdMustChange: TRUE
pwdSafeModify: FALSE #这里如果修改为TRUE,自助修改密码会出现问题。
pwdReset: TRUE
sn: default value
dn: cn=low_security,ou=pwpolicies,dc=test,dc=net,dc=cn
cn: low_security
objectClass: pwdPolicy
objectClass: person
pwdAllowUserChange: TRUE
pwdAttribute: userPassword
pwdExpireWarning: 259200
pwdFailureCountInterval: 0
pwdGraceAuthNLimit: 5
pwdInHistory: 5
pwdLockout: TRUE
pwdLockoutDuration: 300
pwdCheckQuality: 1
pwdMaxAge: 2592000
pwdMaxFailure: 5
pwdMinAge: 0
pwdMinLength: 6
pwdMustChange: TRUE
pwdSafeModify: FALSE
pwdReset: TRUE
sn: low value
下面是每个条目的规则解释
pwdAllowUserChange:允许用户修改其密码
pwdAttribute, pwdPolicy:对象的一个属性,用于标识用户密码。默认值(目前唯一支持的)是userPassword
pwdExpireWarning:密码过期前警告秒数
pwdFailureCountInterval:多久时间后重置密码失败次数, 单位是秒
pwdGraceAuthNLimit:密码过期后不能登录的天数,0代表禁止登录。
pwdInHistory:开启密码历史记录,用于保证不能和之前设置的密码相同。
pwdLockout:定义用户错误密码输入次数超过pwdMaxFailure定义后, 是否锁定用户, TRUE锁定(默认).
pwdLockoutDuration:密码连续输入错误次数后,帐号锁定时间。
pwdMaxAge:密码有效期,到期需要强制修改密码, 2592000是30天 pwdMaxFailure:密码最大失效次数,超过后帐号被锁定。
pwdMinAge:密码最小有效期, 默认为0, 用户随时更改密码, 如果定义了, 用户在离上次更改密码 + 定义的时间之内不能 更改密码
pwdMinLength:用户修改密码时最短的密码长度
pwdMustChange:用户在帐户锁定后由管理员重置帐户后是否必须更改密码, 并且只有在pwdLockout为TRUE时才相关, 如果值为FLASE(默认值), 管理员帮用户解锁用户后, 用户不必更改密码, 如果为TRUE, 就必须更改密码。如果使用 pwdReset来解锁用户, 其值将覆盖此属性
pwdSafeModify:该属性控制用户在密码修改操作期间是否必须发送当前密码。如果属性值为FALSE(缺省值),则用 户不必发送其当前密码。如果属性值为TRUE,那么修改密码值时用户必须发送当前密码。
pwdLockoutDuration:帐号锁定后,不能自动解锁,此时需要管理员干涉
8.3:测试密码规则是否生效
8.3.1:我们创建个用户测试密码规则
dn: uid=t1234,ou=Group,dc=test,dc=net,dc=cn
uid: t1234
cn: t1234
sn: t1234
mail: t1234@test.net.cn
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
objectclass: radiusprofile
radiustunnelmediumtype: IEEE-802
radiustunnelprivategroupid: 1234
radiustunneltype: VLAN
userPassword: 123456
shadowLastChange: 18222
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1313
gidNumber: 500
homeDirectory: /home/t1234
8.3.2:使用ldapadd增加条目
ldapadd -x -D "cn=acadmin,dc=test,dc=net,dc=cn" -w qwer@1234 -f ~/test2.ldif
adding new entry "uid=t1234,ou=Group,dc=test,dc=net,dc=cn"
8.3.3:虽然我们刚才添加用户时使用的是明文密码,但是在生成用户时,已经自动将明文密码加密了。

8.3.4:查看自助修改密码时密码策略是否生效

8.3.5:点击提交后,服务器拒绝了我们的密码

8.3.6:我们测试一下8位密码

这时密码的加密策略也设置完成了。接下来就是对接freeradius啦。
(这里原本计划使用samba的密码来加密,使用samba密码后,自助修改密码的程序不能修改密码了,我想应该是密码的字段发生了变化导致的,我的目的就是密码可以加密,不是明文就行,既然目标很简单,那就换一种实现方式了。)
09:对接freeradius并实现openldap+freeradius+keepalived高可用
上回我们已经搭建好了ldap环境,并且做了高可用状态。密码也可以自助修改了,这次我们把radius对接到ldap上,来实现动态vlan的下发。
9.1:配置freeradius
9.1.1:安装软件
上次我们已经安装好了freeradius安装包。
9.1.2:配置ldap的schema
上次我们已经在slapd.ldif里加载了freeradius的schema。
9.1.3:编辑/etc/raddb/mods-available/ldap ldap模块配置文件。
[root@localhost ~]# cat /etc/raddb/mods-available/ldap | grep -v "#"|grep -v "^$"
ldap {
server = 'localhost' #ldap server ip
port = 636 #ldap server port
identity = 'cn=acadmin,dc=test,dc=net,dc=cn' #ldap admin dn
password = 123456 #ldap admin passwd
base_dn = 'dc=test,dc=net,dc=cn' #ldap dn
sasl {
}
update {
control:Password-With-Header += 'userPassword' #radius去ldap继承用户信息里的属性
control:NT-Password := 'ntPassword'
reply:Reply-Message := 'radiusReplyMessage'
reply:Tunnel-Type := 'radiusTunnelType' #这个是隧道类型 VLAN
reply:Tunnel-Medium-Type := 'radiusTunnelMediumType' #这个是协议类型 IEEE-802
reply:Tunnel-Private-Group-ID := 'radiusTunnelPrivategroupId' #这个是 vlan id
}
user {
base_dn = "${..base_dn}"
filter = "(uid=%{%{Stripped-User-Name}:-%{User-Name}})"
sasl {
}
}
group {
base_dn = "${..base_dn}"
filter = '(objectClass=posixGroup)'
membership_attribute = 'memberOf'
}
profile {
}
client {
base_dn = "${..base_dn}"
filter = '(objectClass=radiusClient)'
template {
}
attribute {
ipaddr = 'radiusClientIdentifier'
secret = 'radiusClientSecret'
}
}
accounting {
reference = "%{tolower:type.%{Acct-Status-Type}}"
type {
start {
update {
description := "Online at %S"
}
}
interim-update {
update {
description := "Last seen at %S"
}
}
stop {
update {
description := "Offline at %S"
}
}
}
}
post-auth {
update {
description := "Authenticated at %S"
}
}
options {
chase_referrals = yes
rebind = yes
res_timeout = 10
srv_timelimit = 3
net_timeout = 1
idle = 60
probes = 3
interval = 3
ldap_debug = 0x0028
}
tls {
}
pool {
start = ${thread[pool].start_servers}
min = ${thread[pool].min_spare_servers}
max = ${thread[pool].max_servers}
spare = ${thread[pool].max_spare_servers}
uses = 0
retry_delay = 30
lifetime = 0
idle_timeout = 60
}
}
vim /etc/raddb/sites-available/site-ldap
server site_ldap {
listen {
ipaddr = 0.0.0.0
port = 1833
type = auth
}
authorize {
update {
control:Auth-Type := ldap
}
}
authenticate {
Auth-Type ldap {
ldap
}
}
post-auth {
Post-Auth-Type Reject {
}
}
}
vim /etc/raddb/sites-enabled/default
vim /etc/raddb/sites-enabled/inner-tunnel 同样的取消掉这两个文件里关于ldap的注释。
750 ldap
...
526 Auth-Type LDAP {
527 ldap
528 }
9.1.4:配置关于动态vlan的选项
vim /etc/raddb/mods-enabled/eap
下面改为yes后,就能够动态获取vlan了
ttls {
... use_tunneled_reply = yes //no改成yes
}
peap {
... use_tunneled_reply = yes
}
9.1.5:将刚才编辑的ldap和site_ldap模块开启
ln -s /etc/raddb/sites-available/site-ldap /etc/raddb/sites-enabled/
ln -s /etc/raddb/mods-available/ldap /etc/raddb/mods-enabled/ldap
9.1.6:radiusd -X测试
使用radiusd -X查看配置有没有问题,没有问题就可以启动服务器了
systemctl restart radiusd
systemctl status radiusd
systemctl enable radiusd
9.1.7:ldap认证测试
使用ldap里的账户测试,看能否认证成功
[root@ldap-radius-master (16:27:10)/etc/openldap]# radtest t1234 12345678 localhost 0 testing123
Sent Access-Request Id 56 from 0.0.0.0:45030 to 127.0.0.1:1812 length 75
User-Name = "t1234"
User-Password = "12345678"
NAS-IP-Address = 10.10.4.238
NAS-Port = 0
Message-Authenticator = 0x00
Cleartext-Password = "12345678"
Received Access-Accept Id 56 from 127.0.0.1:1812 to 0.0.0.0:0 length 38
Tunnel-Type:0 = VLAN
Tunnel-Medium-Type:0 = IEEE-802
Tunnel-Private-Group-Id:0 = "1234"
这里在设置副节点时,也要测试一下副节点的freeradius能否对主节点的openldap进行对接认证。
[root@ldap-radius-slave (22:40:17)/etc/raddb]# radtest t1234 qwer@1234 10.10.4.240 0 test808
Sent Access-Request Id 244 from 0.0.0.0:40059 to 10.10.4.240:1812 length 75
User-Name = "t1234"
User-Password = "qwer@1234"
NAS-IP-Address = 10.10.4.239
NAS-Port = 0
Message-Authenticator = 0x00
Cleartext-Password = "qwer@1234"
Received Access-Accept Id 244 from 10.10.4.240:1812 to 0.0.0.0:0 length 38
Tunnel-Type:0 = VLAN
Tunnel-Medium-Type:0 = IEEE-802
Tunnel-Private-Group-Id:0 = "1234"
返回Access-Accept 就是认证成功了 没有认证成功的话,返回去看看配置文件有没有问题,或者密码有没有问题
9.1.8:设置radius客户端授权网段
client all { #client后面是网段名称
ipaddr = 0.0.0.0/0 #设置可认证网段
secret = test808 #设置秘钥
require_message_authenticator = no #和交换机的兼容性有关
}
然后重启服务
systemctl restart radiusd
10:
11:客户端认证测试
在交换机上配置radius认证,然后连接WiFi测试,看认证后网段有没有变化



评论区